Cyber strategies need to extend beyond the facility to reduce third-party supplier threat risks. Data center executives should apply robust, consistent supply chain risk management practices to critical data center technologies

Michael O'Neil
Michael O'Neil is a Contributing Analyst for the Uptime Network. He has 30 years’ experience as a technology analyst and consultant. Prior to joining Uptime, he was the research lead in the Office of the CISO at Stratascale (an SHI company), where he wrote the Amazon best-seller "The Executive Guide to Zero Trust."
moneil@uptimeinstitute.com
Latest Research
Cybersecurity strategies often evolve organically: tools are added, requirements change, and the result is a lack of coherent structure. Cybersecurity professionals can benefit from adopting frameworks to organize these activities
Policies and procedures translate cybersecurity management objectives into the activities that protect data centers. But what steps should operators take to establish a comprehensive approach to implement these policies?
Data center cybersecurity risks need to be managed in line with corporate objectives and across a wide range of cyber adversaries and threats. This means understanding the organizational risk tolerance and being able to identify the best options for
Data center cyber governance requires all key tasks to be identified, and that specific individuals are accountable for each task. Effective cybersecurity governance defines how key assets are protected and the roles that hold responsibility.
Good data center governance provides a foundation for effective data center cybersecurity. How should data center leaders structure an approach that optimizes the resources needed to safeguard data centers?
Identifying the extent of security requirements is a critical first step in building a viable data center cybersecurity strategy. Data center managers should identify and answer essential questions to implement an effective playbook.
Operators often resist giving third parties access to OT data to limit vulnerabilities. Nevertheless, some colocation customers require this access - as will emerging AI tools - but the OT air-gap should not be bridged lightly.
Data center managers are squeezed between complexity arising from digital innovation and the need for secure and reliable service delivery. Is it possible to minimize risk while enabling business innovation?
Identifying the extent of security requirements is a critical first step in building a viable data center cybersecurity strategy. Data center managers should identify and answer essential questions to implement an effective playbook.
Most cyberattacks are sudden and target financial gain. Attacks on data centers and critical infrastructure can be very different. State-sponsored hackers use varied and sophisticated tactics in support of geopolitical goals.
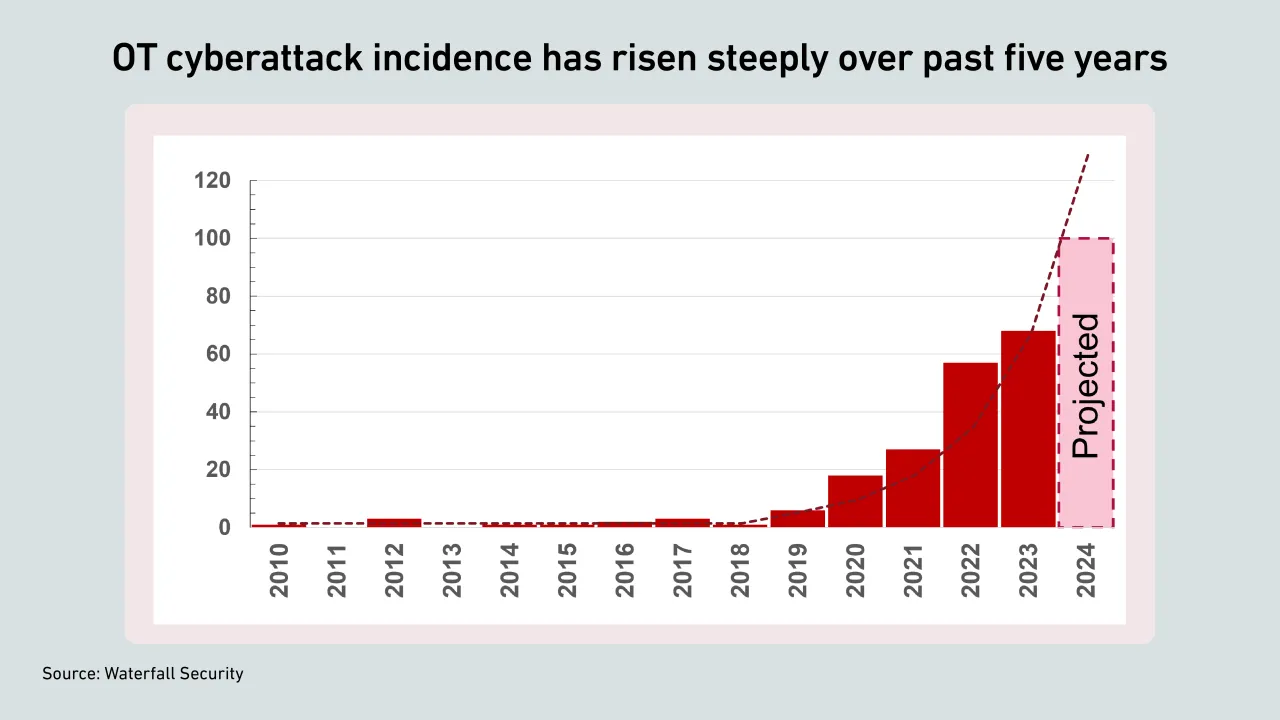
Cyberattacks on operational technology (OT) systems are rising, and OT failure could be catastrophic for data centers. Managers need to understand the nature of the threat and the defense options to protect their critical environments.
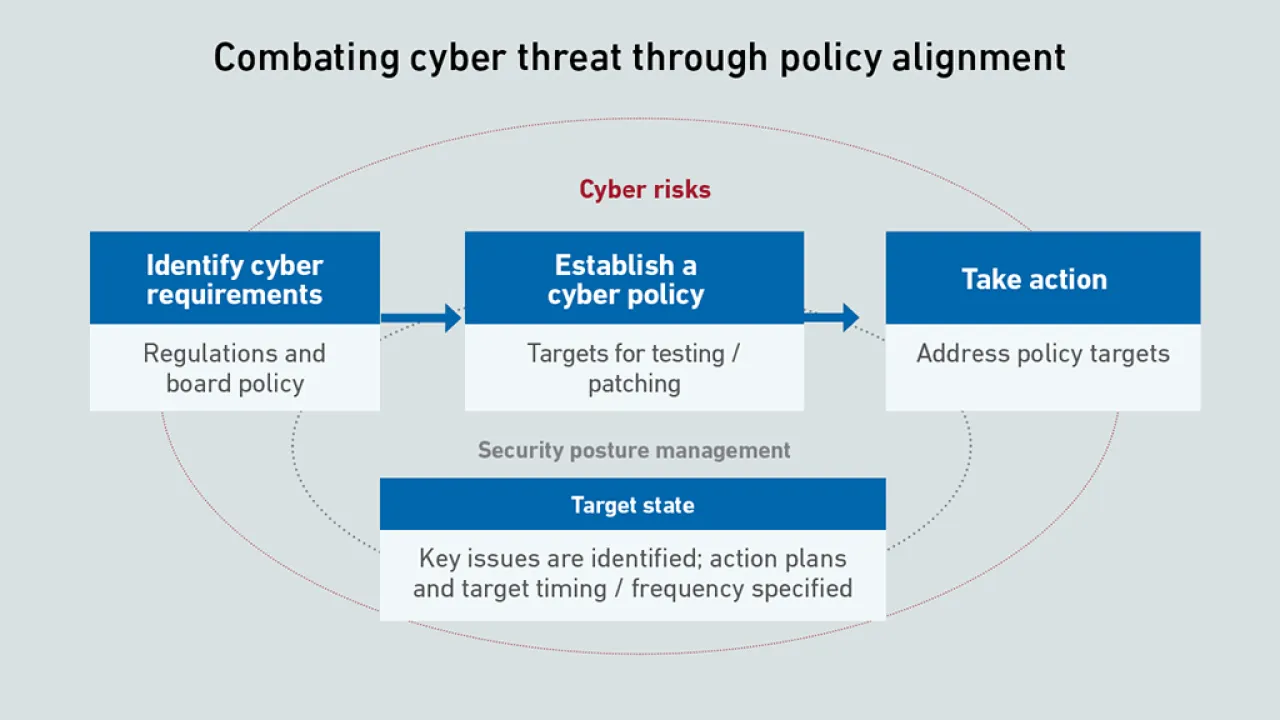
Organizations develop strict security policies and practices to reduce exposure to cyberattacks. An ineffective policy only increases the cyber risk both to the data center and across IT in general.