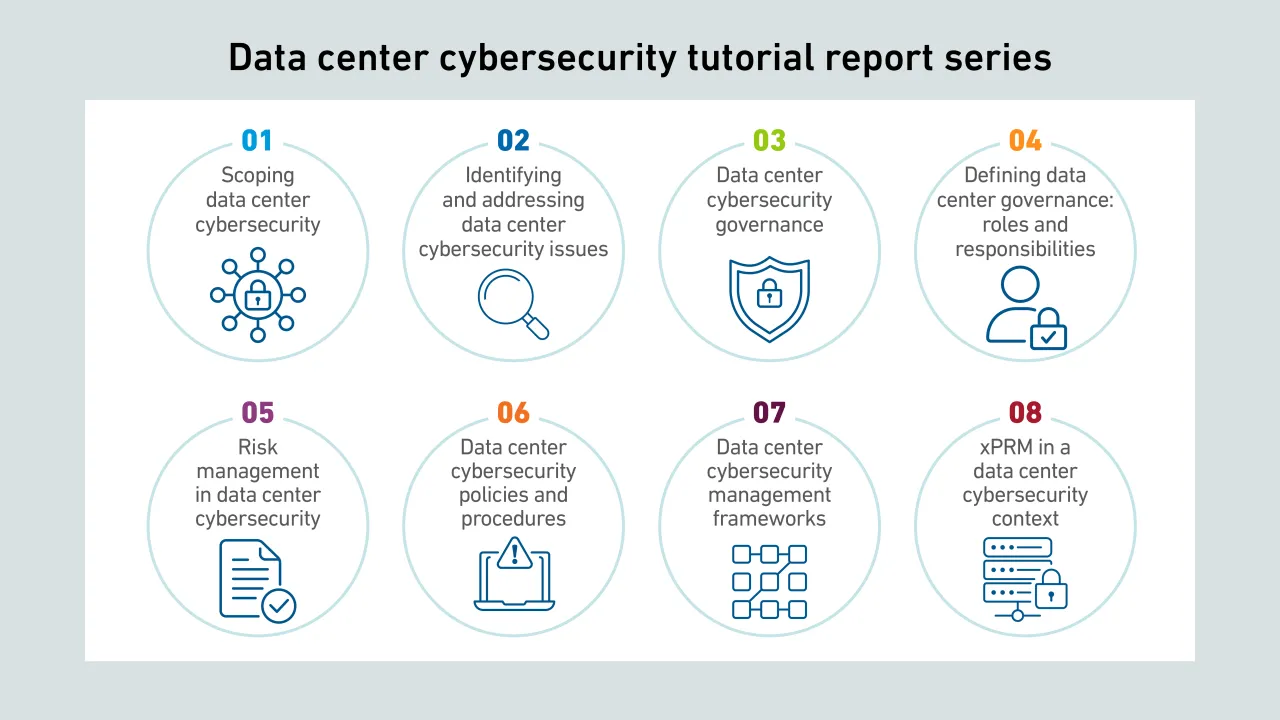
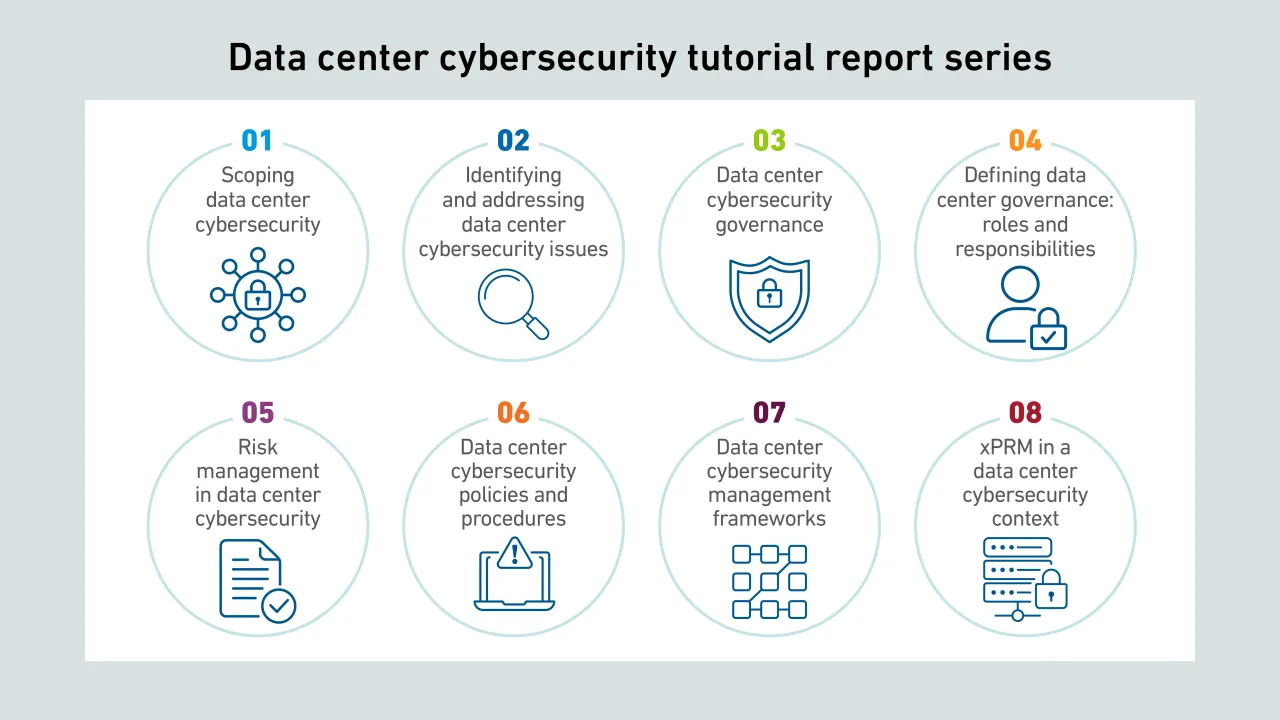
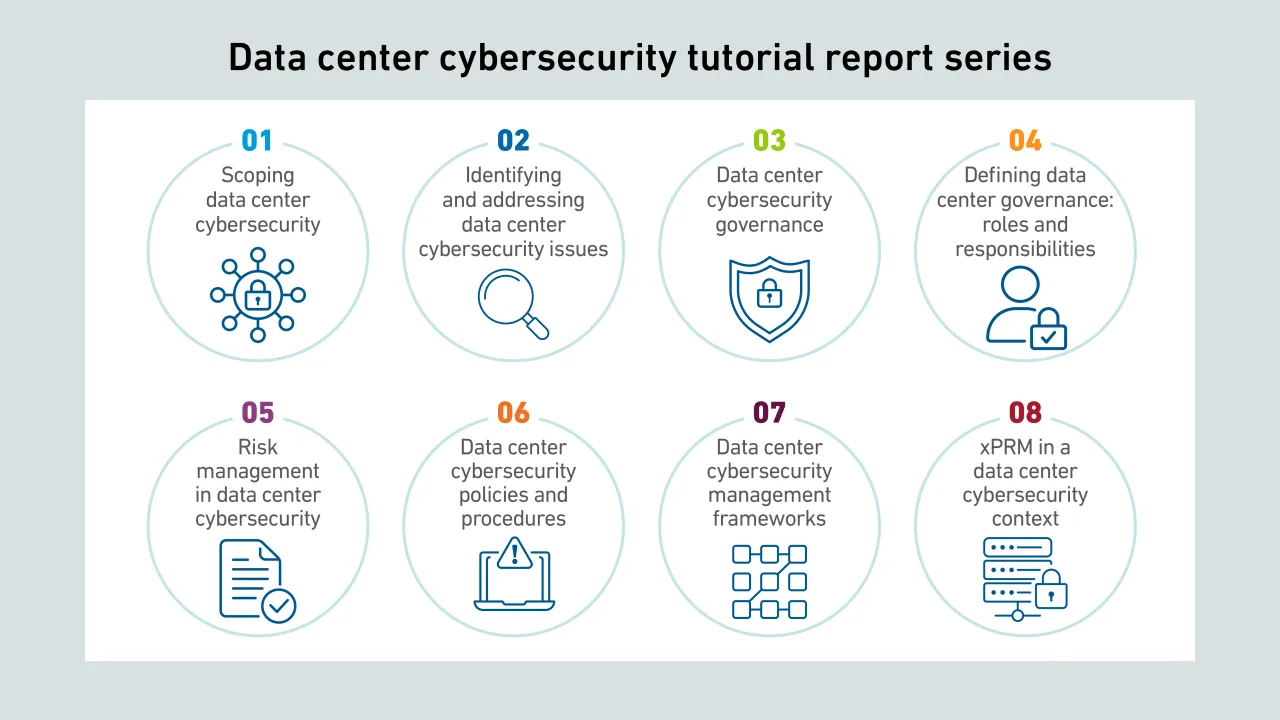
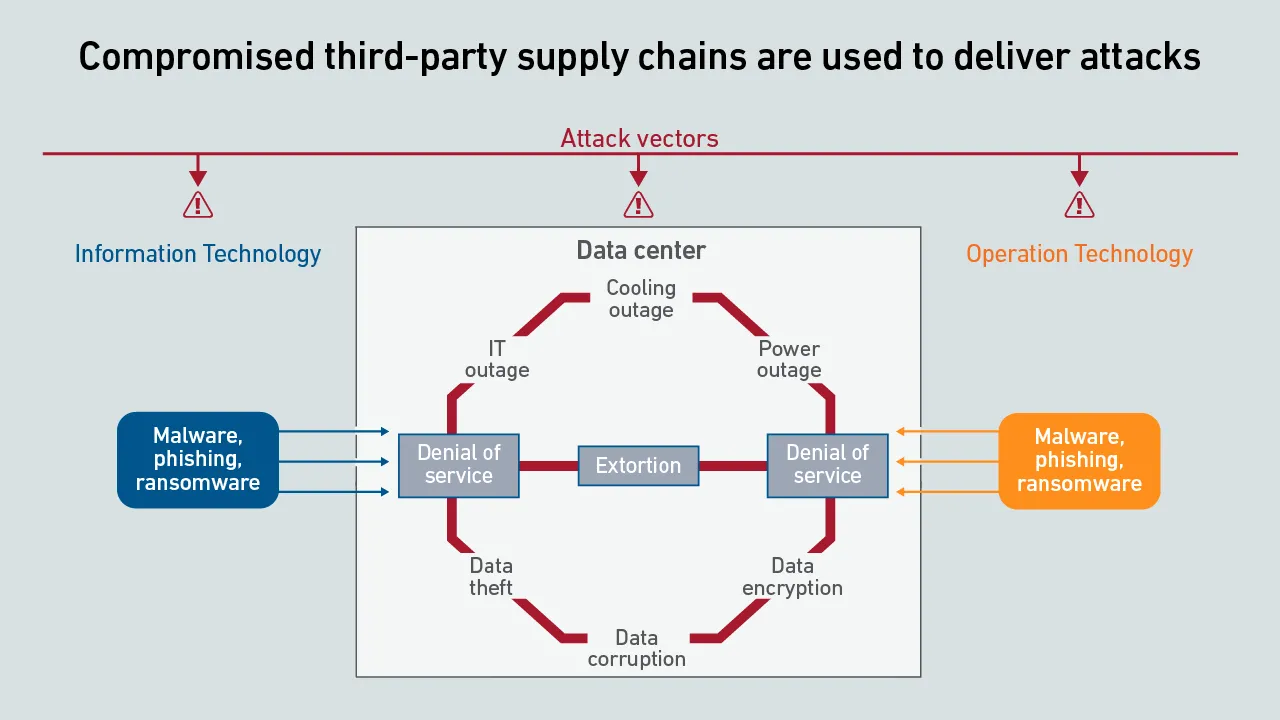
Cybercriminals increasingly target supply chains as entry points for coordinated attacks; however, many vulnerabilities have been overlooked by operators and persist, despite their growing risk and severity.
filters
Explore All Topics
Managing third-party risk effectively is challenging. But what if you could have a real-time understanding of your vendors' cybersecurity posture? In this webinar, we'll show you how to assess vendor cybersecurity capability to:Assess risk quickly…
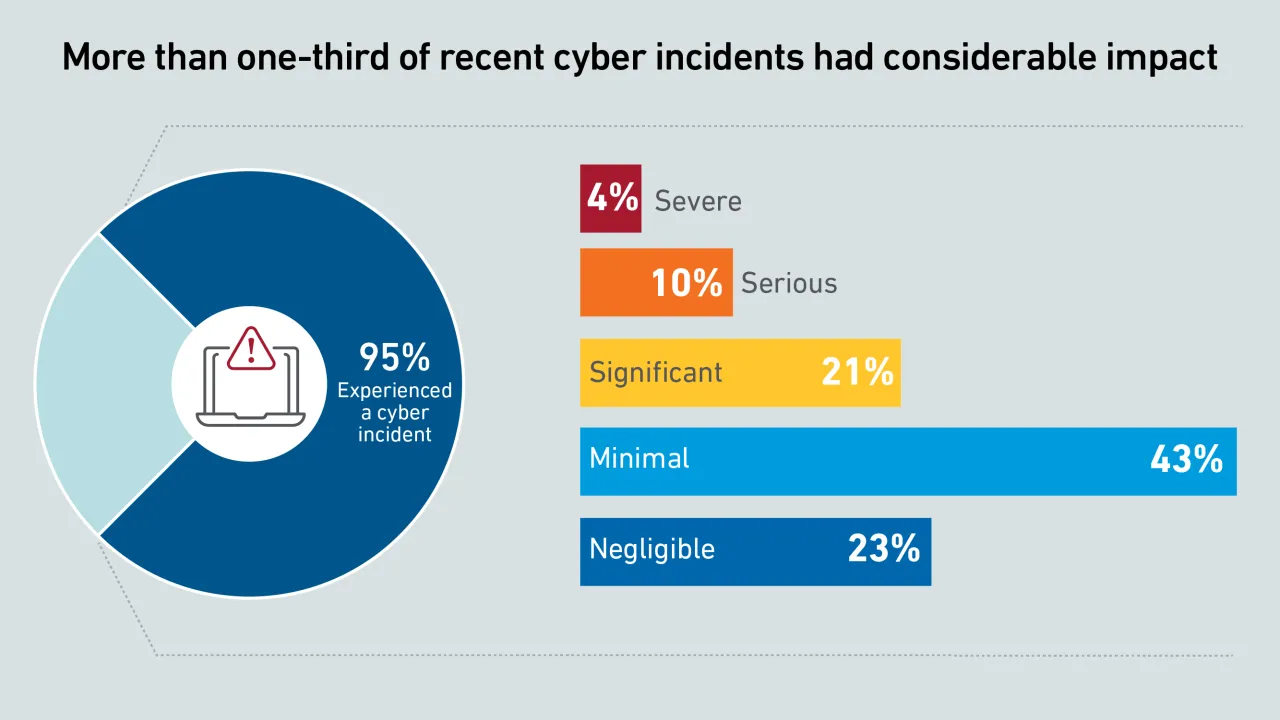
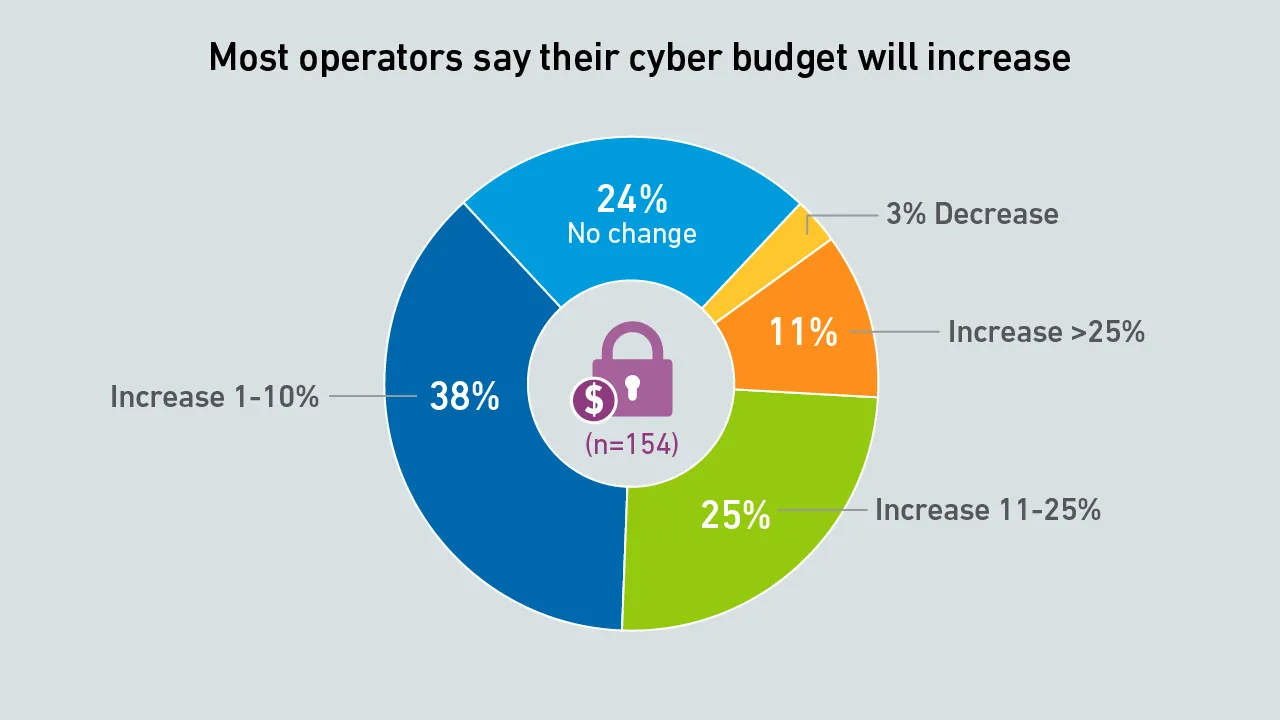
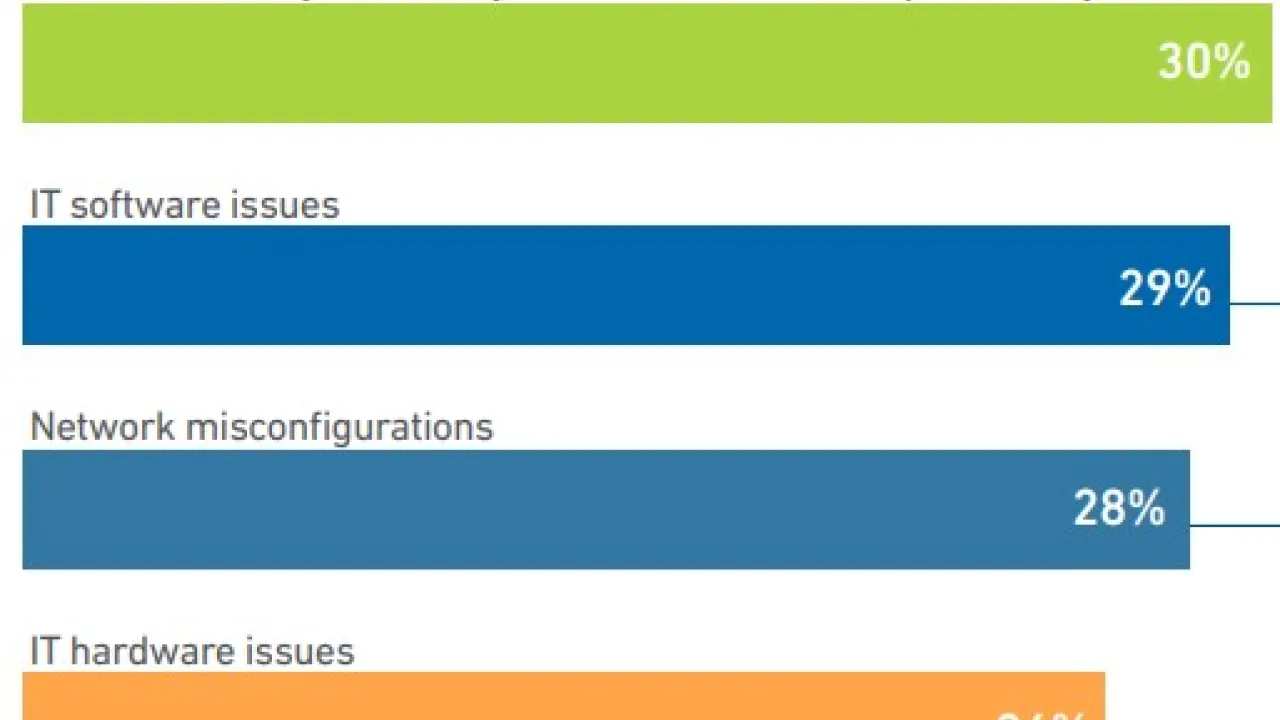
Cybersecurity issues remain a major threat to the industry. This report highlights findings from the Uptime Institute Data Center Security Survey 2025, including costs and the persistence of IT software and network configuration issues.
Results from Uptime Institute's 2025 Security Survey (n=982), now in its 3rd year, explore major cybersecurity issues facing data centers, as well as the IT and OT systems used to operate critical infrastructure.The attached data files below provide…
This webinar discussed the latest cyberattack trends targeting digital infrastructure and explored common attack vectors against IT, OT, and IoT systems, analyzing the techniques used by malicious actors to compromise systems and disrupt data center…
Data center operators are increasingly aware that their operational technology systems are vulnerable to cyberattacks. Recent incident reports show a rise in ransomware attacks, which pose significant risks to data centers
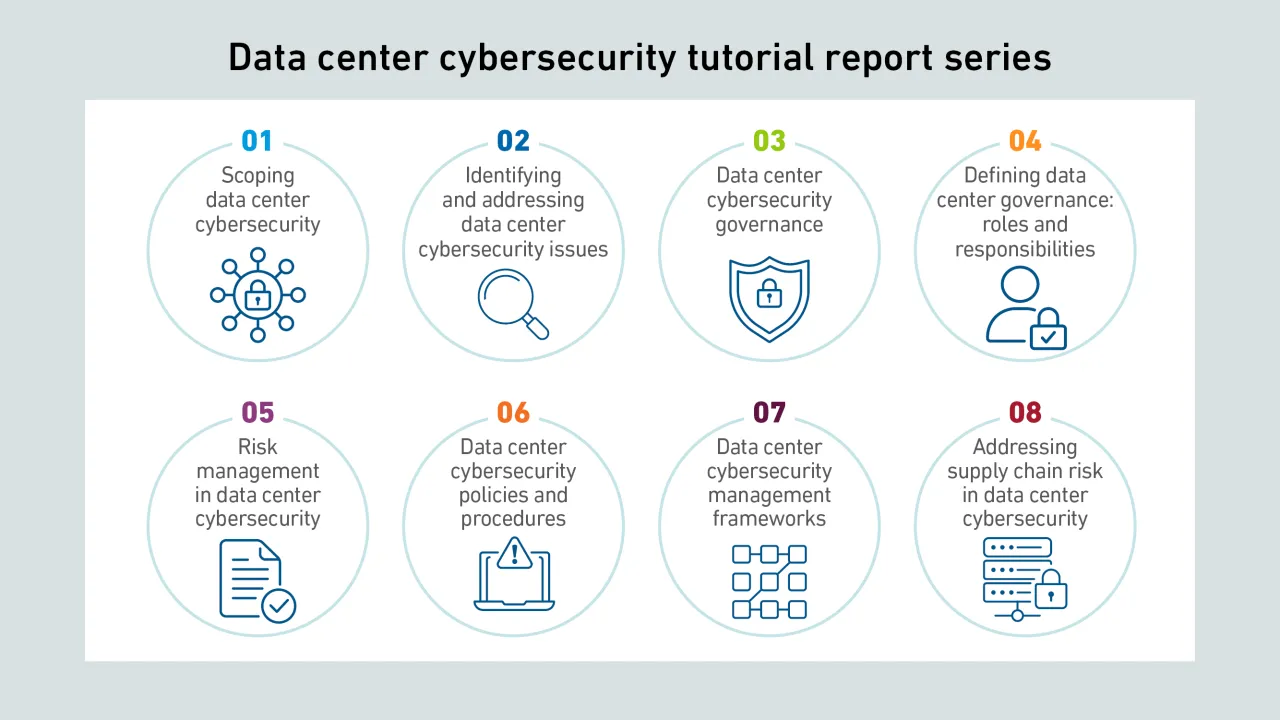
Cybersecurity has traditionally not been a key focus of attention for data center operators. But cyber incidents are on the rise and concerns are growing. Unaddressed vulnerabilities leave operators at increasing risk from evolving threats.
Human error is an increasingly exploited weakness by cyberattackers, leading to data center security breaches and greater risk for enterprises and operators.
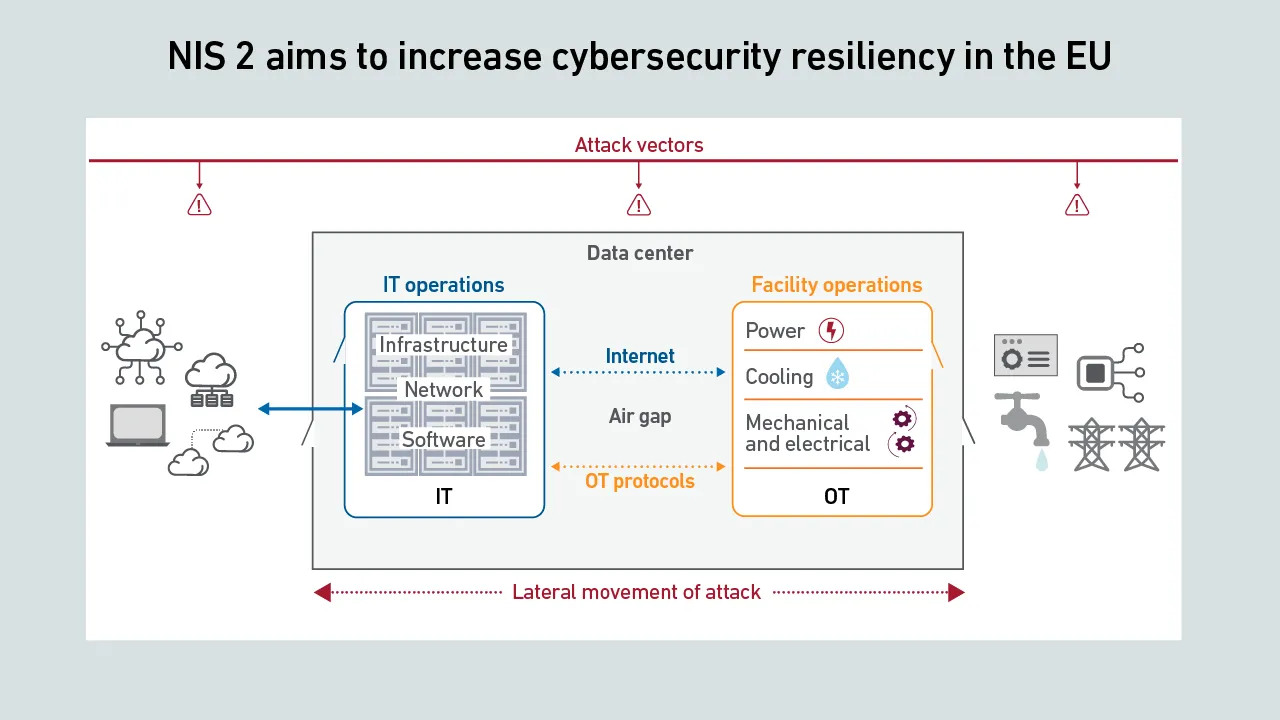
European cybersecurity regulations have become effective and will have a major impact on both critical infrastructures and their cybersecurity management. This webinar will discuss the NIS2 Directive, the European Union’s updated cybersecurity…
The EU's NIS 2 directive requires all organizations operating in Europe to comply with 10 essential cybersecurity measures, but many data center operators remain unprepared.
Cyber strategies need to extend beyond the facility to reduce third-party supplier threat risks. Data center executives should apply robust, consistent supply chain risk management practices to critical data center technologies
Results from the Uptime Institute Security Survey 2024 highlight the different cybersecurity approaches used by operators against a widening range of threats.
Cybersecurity strategies often evolve organically: tools are added, requirements change, and the result is a lack of coherent structure. Cybersecurity professionals can benefit from adopting frameworks to organize these activities
Policies and procedures translate cybersecurity management objectives into the activities that protect data centers. But what steps should operators take to establish a comprehensive approach to implement these policies?
Data center cybersecurity risks need to be managed in line with corporate objectives and across a wide range of cyber adversaries and threats. This means understanding the organizational risk tolerance and being able to identify the best options for
 John O'Brien
John O'Brien

 Antonio Ramos
Antonio Ramos
 Lanre Rotimi
Lanre Rotimi
 Rose Weinschenk
Rose Weinschenk
 Paul Carton
Paul Carton
 Anthony Sbarra
Anthony Sbarra
 Laurie Williams
Laurie Williams



 Michael O'Neil
Michael O'Neil
 Douglas Donnellan
Douglas Donnellan